
Architecture for detecting insider threats using Structural Anomaly... | Download Scientific Diagram
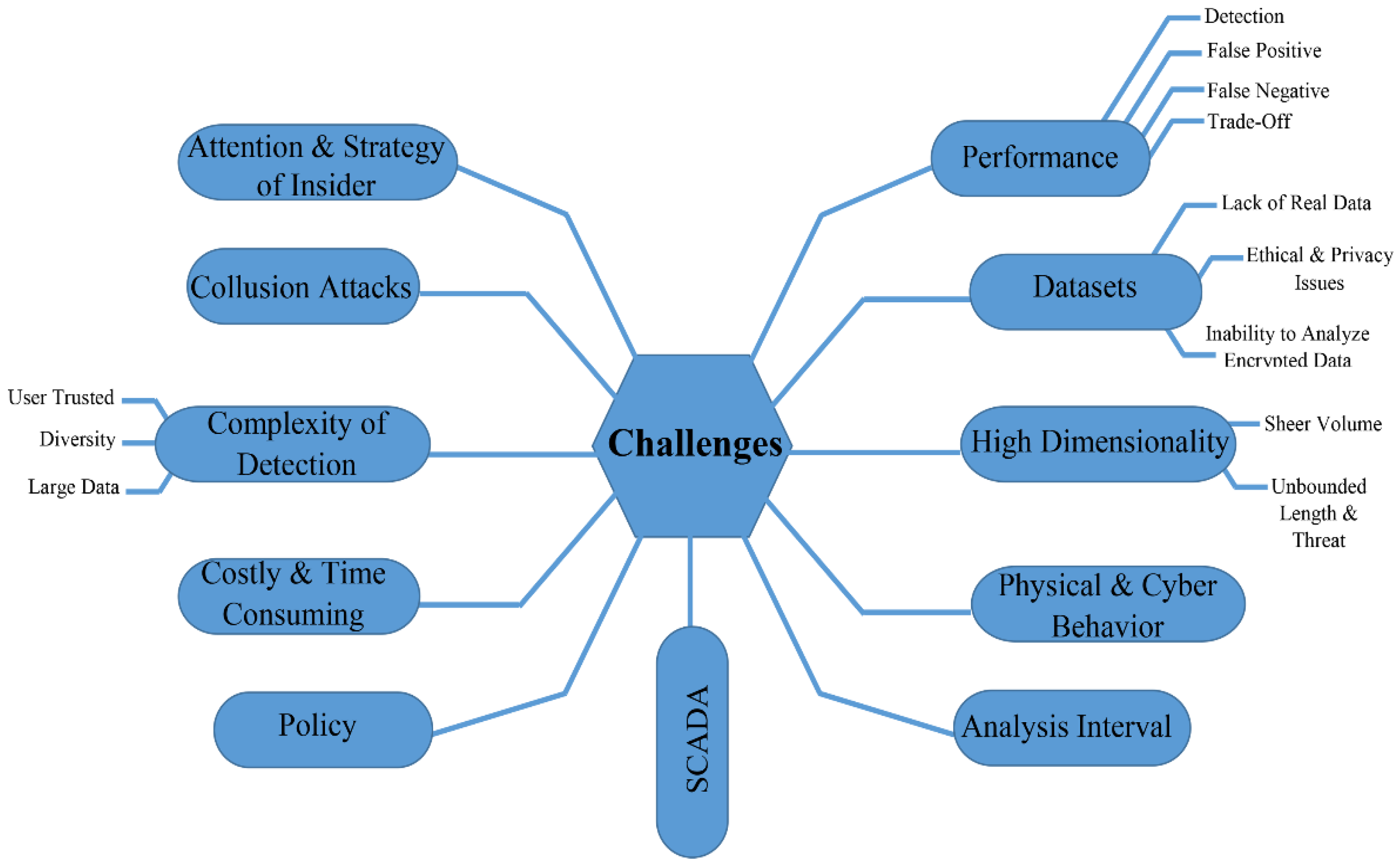
Applied Sciences | Free Full-Text | A Review of Insider Threat Detection: Classification, Machine Learning Techniques, Datasets, Open Challenges, and Recommendations

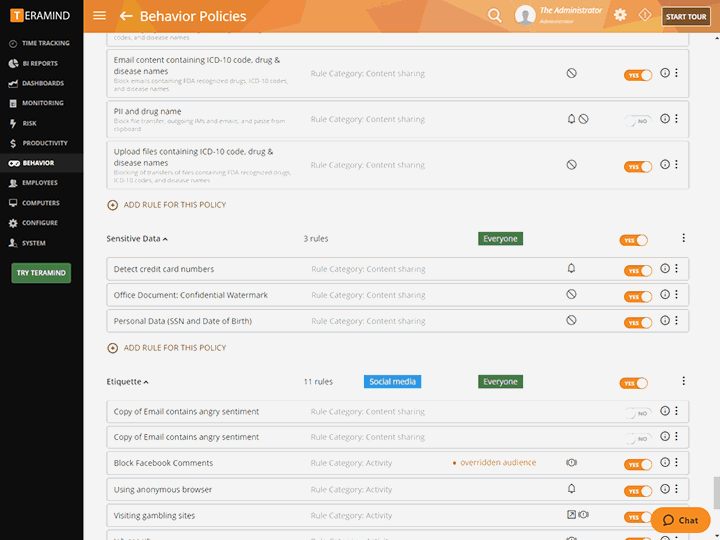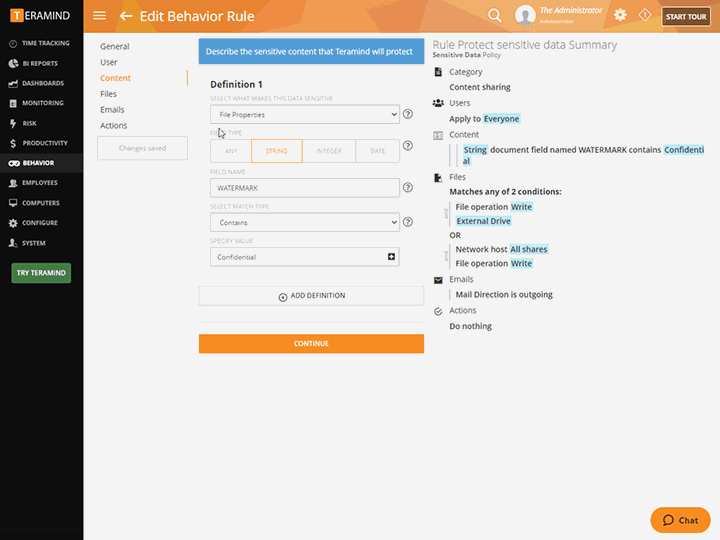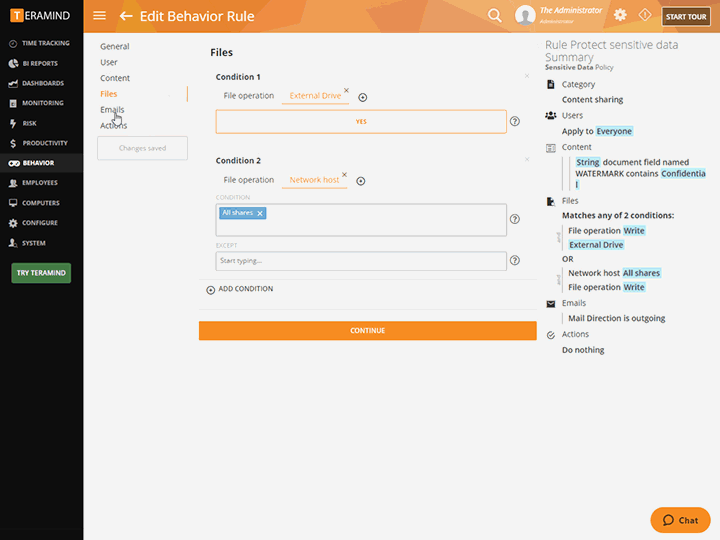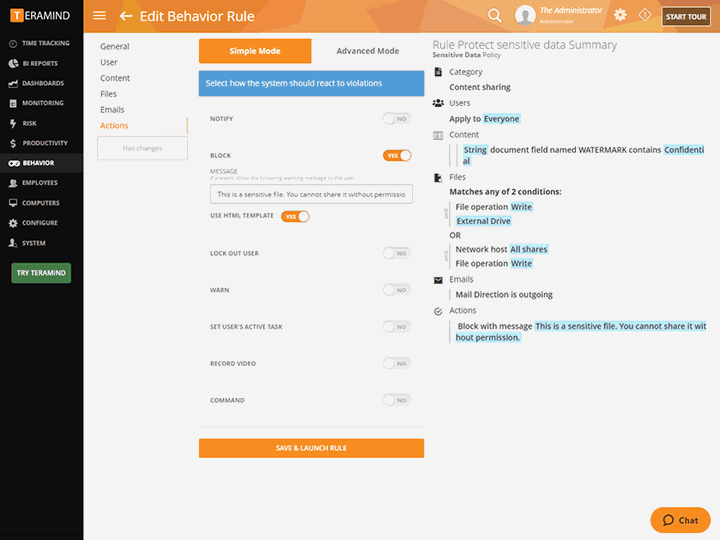
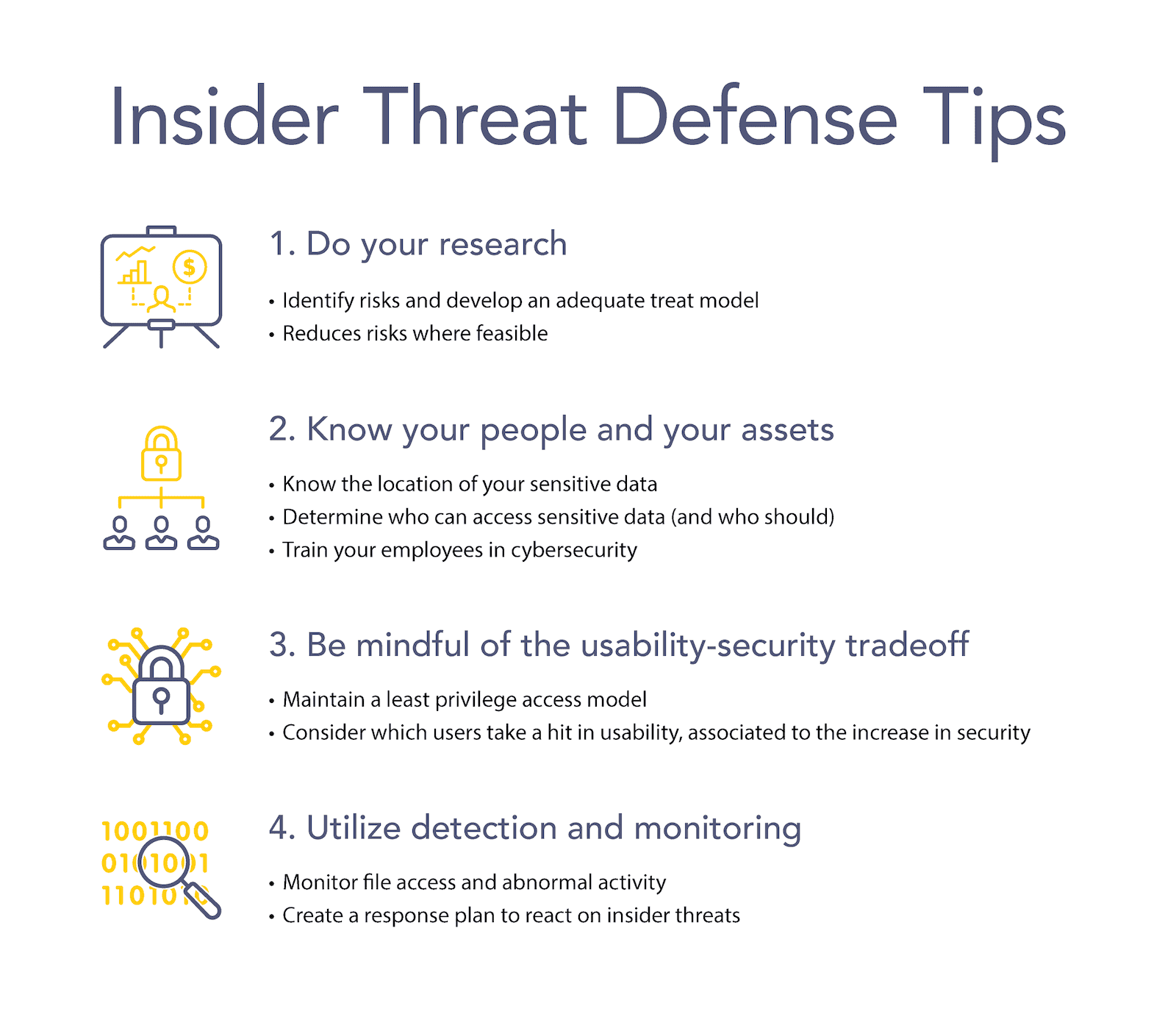
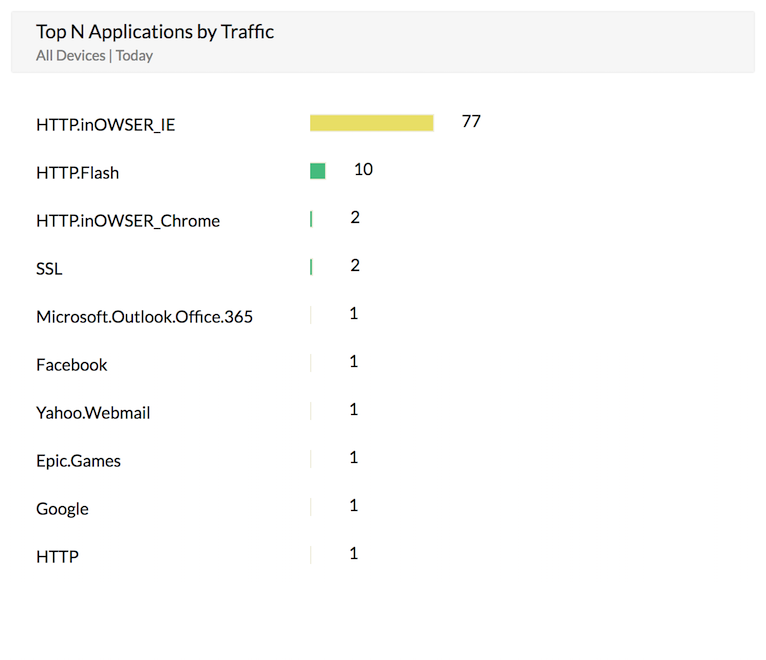
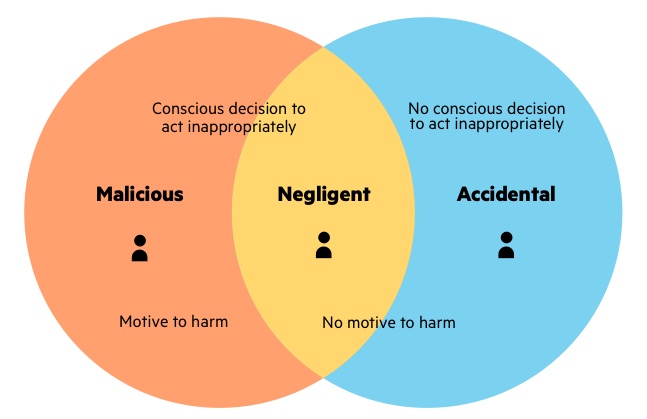
![PDF] Classification of Insider Threat Detection Techniques | Semantic Scholar PDF] Classification of Insider Threat Detection Techniques | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d580c24b9601e240d0161fbc47c7075bbe2fc59d/1-Figure1-1.png)





![Building an Insider Threat Program [10-step Checklist] | Ekran System Building an Insider Threat Program [10-step Checklist] | Ekran System](https://ekran_site_uploads.storage.googleapis.com/wp-content/uploads/2023/09/12232127/pic-7-How-to-Build-an-Insider-Threat-Program-10-step-Checklist.png)

