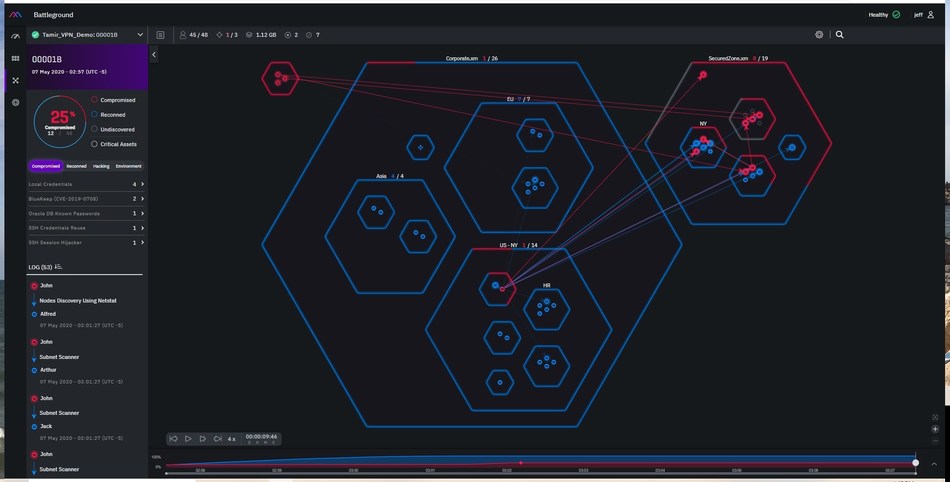
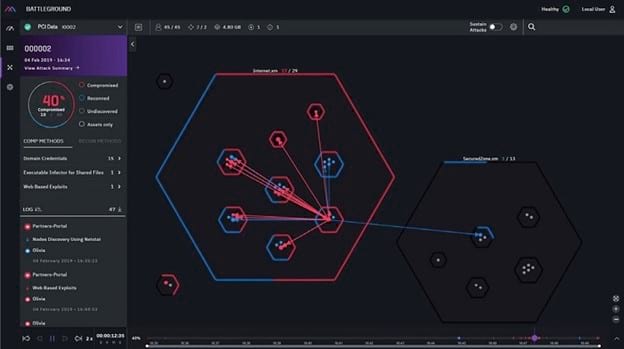
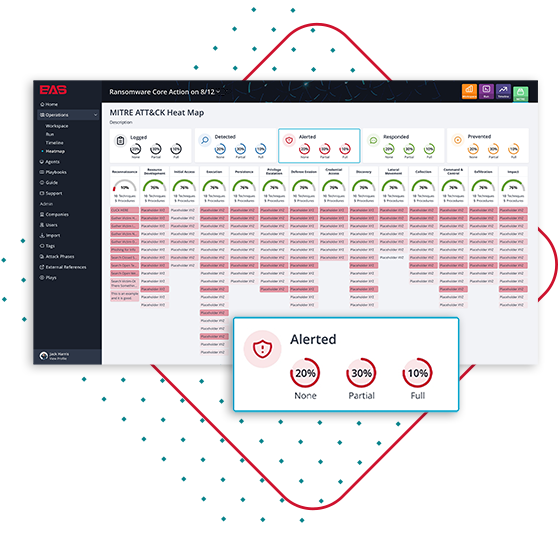
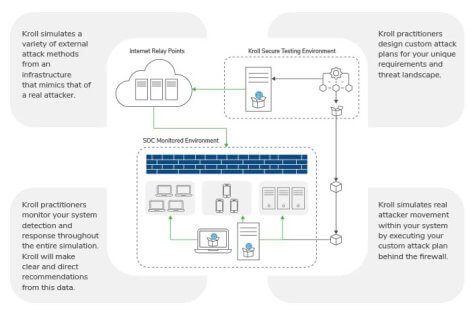
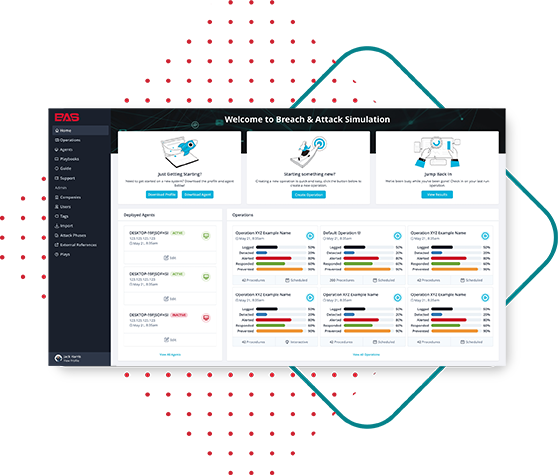
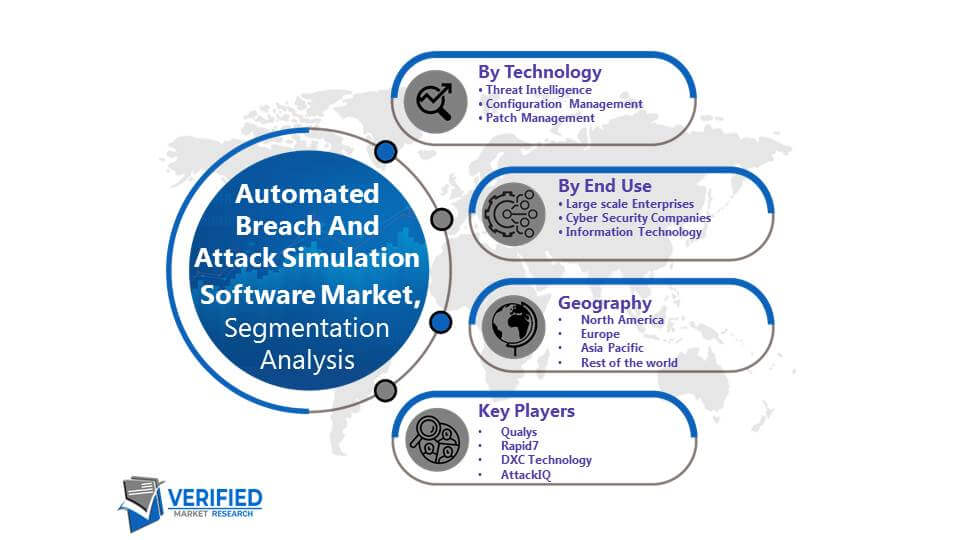
Breach and Attack Simulation Tools Market Customer Insights, Statistical Data Solutions With Research Analysis Globally

Picus Security is a 2024 Customers' Choice for Breach and Attack Simulation Tools on Gartner® Peer Insights™
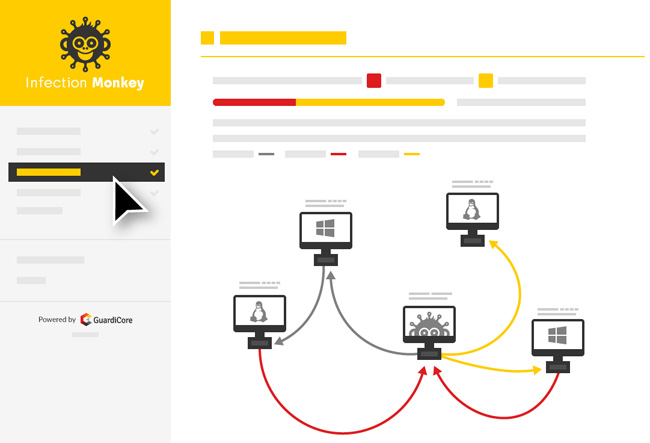
Open source breach and attack simulation tool Infection Monkey gets new features - Help Net Security